Updates on OpenCTI: Introducing the RST WHOIS API Connector
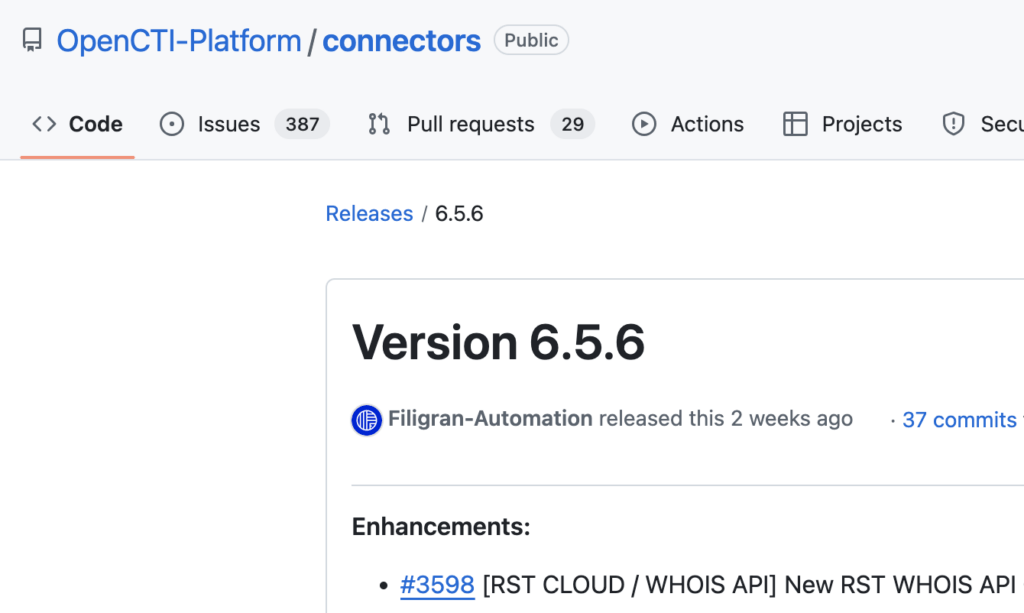
We are excited to announce significant updates to our integration with OpenCTI! As part of our ongoing commitment to enhancing threat intelligence capabilities for our users, we have introduced the RST WHOIS API connector, now available in the latest OpenCTI release, version 6.5.6. This addition, combined with other RST Cloud OpenCTI connectors, represents a crucial […]
Updates on OpenCTI: Introducing the RST WHOIS API Connector Read More »